
Author: Dr Emma Taylor, Head of Digital Safety
An award-winning Chartered Engineer, with more than 30 years of experience across space, energy and transport sectors. Over her career, she has led an ISO team developing a standard to mitigate space debris, assembled safety cases for multi-billion pound UK offshore HSE regulated developments and evaluated the safety impact of changes to the rail network. As Head of Digital Safety at RazorSecure, she is leading the integration of safety and cyber security requirements within rail, including leading a UK government funded research programme on Digital Maintenance
As someone that has worked in safety for many years, from space to rail, one of the questions that I am asked more and more frequently is “where do we start with cyber security?” which is not surprising considering many of the recent media headlines. One way to start is to instead think of ‘digital safety’, which is at heart ensuring that digital components on the network meet their required function and support safe operations.
All of us design and deliver solutions that integrate into one great big operating transport system. If you work in rail, how the overall rail network fits together sets the context for what you do, and so it’s perfectly natural to ask about what’s happening elsewhere and how it impacts you.
This ‘system wide’ thinking and asking “what if?” is also a good place to start. In rolling-stock there are lots of moving parts and information flows through many connections. The information is also used in different ways.
It can seem a daunting task to get a handle on the overall system.
This is where focussing on visibility of a system comes into its own, both as an integrated part of cyber security and as a cornerstone for safety of all elements of a rail network, both physical and digital. If you don't have visibility of a system to be monitored, if you can't shine a spotlight on what the system is and what it's doing, how can you secure it? Similarly, if a system is not secure, it is hard to make the case that it is safe. Taking this focus on visibility of what's happening frames a clear and simple question that you can ask yourself, without being a technical specialist - “do I know what is going on?”.
Monitoring to answer this question is embedded in all aspects of rail operations, from asset management to incident reporting. For example, in the UK there is an industry-wide programme to collect data and generate annual safety reports showing trends and highlighting areas for action.
Monitoring is of course part of licensing, and implemented through a range of frameworks. The ORR, the UK regulator, uses a Risk Management Maturity Model (RM3) which covers monitoring, audit and review.
You of course need to monitor people, competency, management systems and their implementation as well as technology and how they work together. This all fits under the umbrella of the PDCA (Plan-Do- Check-Act) cycle. This approach to monitoring is based on events happening, being detected and then assessed. These events may not directly lead to accidents, they may instead be near misses of incidents that may indicate an underlying root cause or emerging trends.
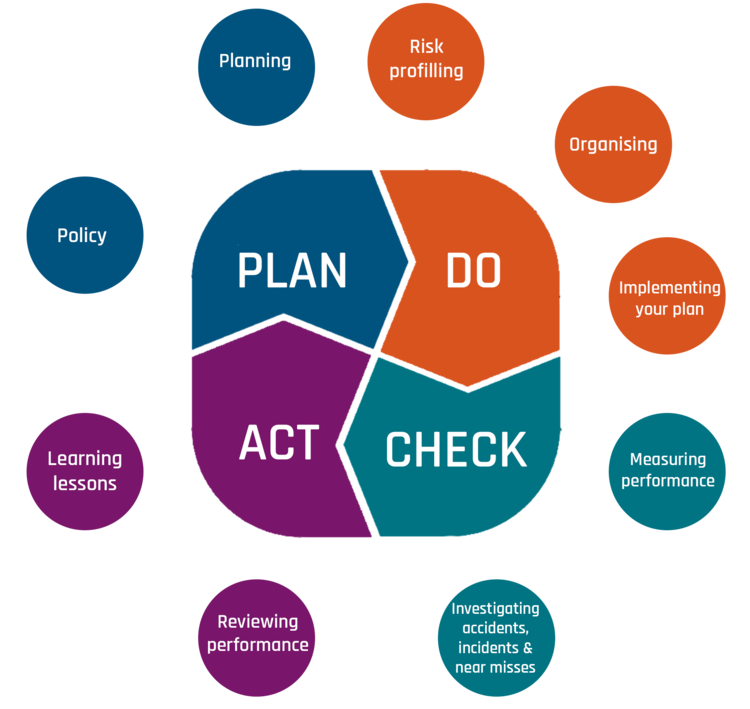
The Plan-Do-Check-Act cycle (HSG 65 2013)
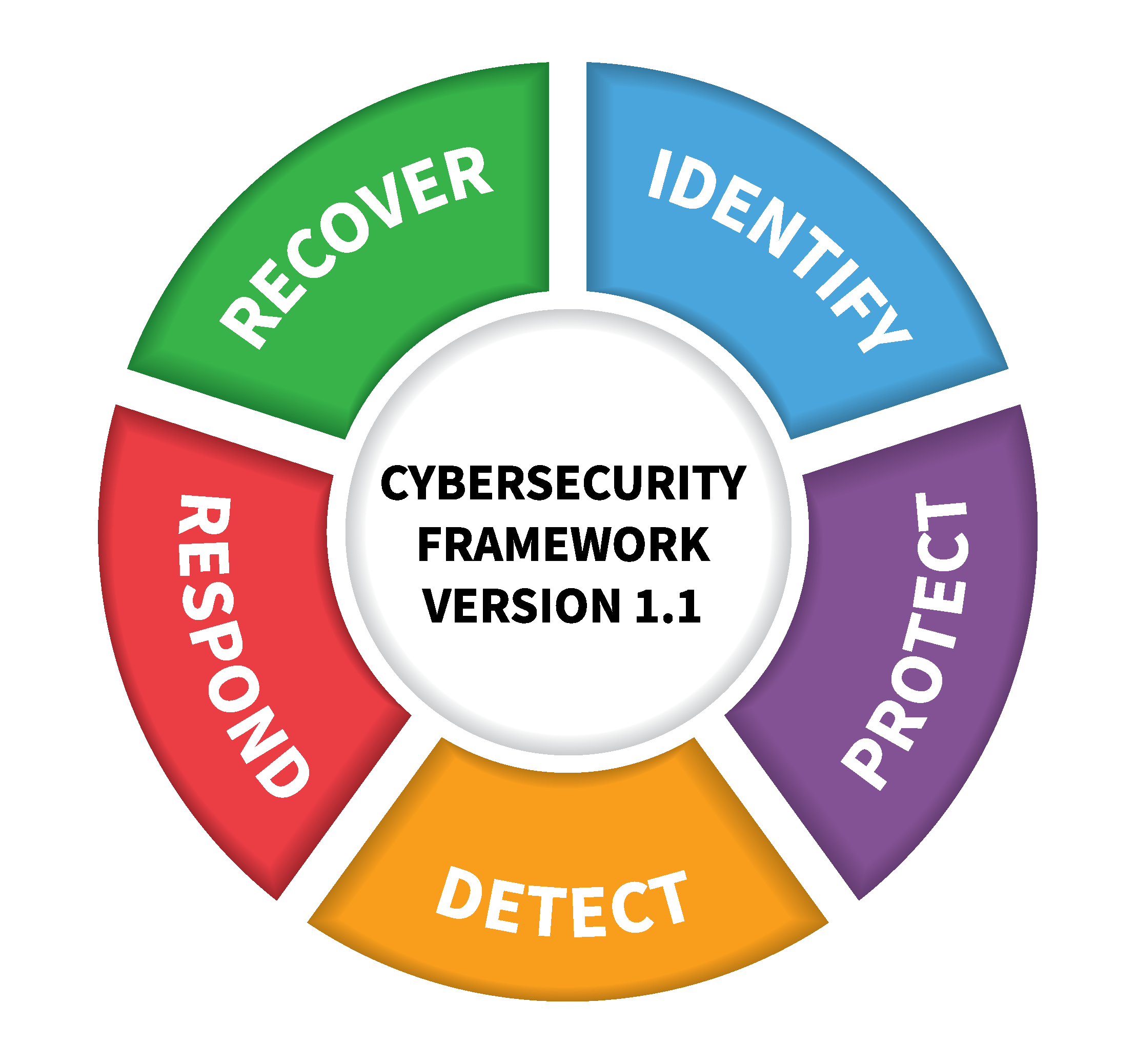
NIST Cyber Security Framework model
Monitoring is an activity which is also integral to cybersecurity as shown in the NIST cyber security framework. The five steps (Identify, Protect, Detect, Respond and Recover) follow a similar iterative approach to the safety Plan-Do-Check-Act. As for safety, not every issue that is detected may lead to an issue being realised. It is equally as important in cyber security as in safety to look for emerging trends and deviations from the norm, perhaps even more so given the complex nature of digital systems.
| IDENTIFY | What processes and assets need protection? |
|---|---|
| PROTECT | What safeguards are available? |
| DETECT | What techniques can identify incidents? |
| RESPOND | What techniques can contain impacts of incidents? |
| RECOVER | What techniques can restore capabilities? |
There is a need to build a bridge between monitoring for safety, and monitoring for cyber security
One aspect is the need for increased focus on visibility of what's going on as part of monitoring. This is because in this 'digital safety' world things are less known, more complicated and prone to more rapid and less predictable change. You need to keep your finger on the pulse, an ongoing watchfulness. In general the cyber security challenges change rapidly and the past can’t be used comfortably to predict the future.
Looking at the complex system-wide architecture of a train, it’s evident that keeping a close eye on all aspects of digital operations makes sense, particularly with this increased focus on understanding of the system as part of monitoring. Visibility, within a OT cyber security context, means understanding what assets you have and their operating conditions, current and past. Without this visibility, you are potentially operating without a clear understanding of your network. An asset inventory is essential. For digital assets, this includes software and firmware code versions, knowing what is connected to what, and understanding the information that is flowing around the network. I sometimes describe it as a ‘digital ring main’, with data being distributed rather than electricity! Looking at a network diagram, the discovery and understanding of what is happening certainly is a more complex challenge than for physical assets, and given that, how can it be achieved?
To enable this ongoing asset visibility, our clients and others use their existing digital rolling stock network configuration to their best advantage, with different systems on different networks (segregation and zones) and digital ‘junction boxes’ to manage the flow of data (firewalls and routers). This gives some protection, and some information, but it doesn’t help highlight what is going wrong to a deep enough level of detail and timeliness.
One improvement is to install some additional monitoring software on the existing network equipment or put an additional security gateway in. This approach has the added benefit of asset discovery through monitoring, giving visibility of the physical and digital infrastructure ‘as is’ and ‘as was’, not just ‘as first installed’.
This enhanced approach helps meet legislative requirements internationally. For example, looking at the framework for cyber security, the EU NIS CAF¹, which in the UK the cyber regulator DfT (Department for Transport) runs in alongside the ORR RM3 (both link to UK law, UK legislation) there is a strong focus on gaining visibility of your systems and devices, continuously monitoring them to detect for threats, and of course recovery from an incident. There are also elements in common with safety; such as governance and management of systems and staff.
It’s a good idea to use both the frameworks as a combined and complete set, as it gives a balanced view of where to focus your priorities and helps you see how visibility and monitoring fit together and act in context with the other things that are done to manage risk.
So where can you start with cyber security?
A comprehensive approach involves following the full process as outlined in standards and procedures, but this can seem daunting.
Take those first steps with a ‘visibility’ approach, this can help with a focus on detection of assets and their continuous monitoring, by following these steps:
-
Look at a railway physical architecture model and identify the systems under your direct control and/or responsibility, and then how they are connected to other systems. Take a digital parts approach.
-
Take both the safety and cyber security management frameworks and carry out a high level screening, considering both physical and digital parts of your network. There will be gaps.
-
New systems and devices can be added or modified at any time. Ask yourself the questions:
-
Do I know what I’ve got? (i.e. assets)
-
Do I know what is going on with them?, and then the follow up..
-
Will I know when things are going wrong?
-
This approach helps you use frameworks, both safety and security, and also increase a focus on digital safety. It’s not going to give a final answer the first time you do it, not least because of the challenge of identifying all the system connections and the system boundary, but fortunately ongoing assessment is a key part of regulatory compliance. Whilst technical solutions such as those provided by RazorSecure can provide a step forward in meeting regulatory requirements, for best results the need to be integrated as part of a management system, such as that outlined in the ORR RM3, with cyber security governance and other arrangements, with examples in the NCSC CAF and the NIST cyber security framework.
This integrated approach across safety and cyber security frameworks brings us back to ‘digital safety’, and the importance of asset visibility and continuous monitoring in ensuring safe and secure operations of our railway networks.
Please get in touch if you have any questions about how our solutions can help you meet your safety and cyber security legal obligations and design and operational requirements.
1. The EU NIS directive has now been replaced by NIS2
Additional viewing
RazorSecure and University of Birmingham’s BCRRE Digital Maintenance Project
RazorSecure Digital Maintenance Gateway (DMG) Product Page
